Member-only story
AWS SOAR: Enhancing Security with Automation

Hi All , This story is open to everyone; non-member readers can click this link to read the story.
First of all, Let me wish you a Very Happy New year 2023 . May you reach all your personal and professional goals.
Today , We will look at AWS SOAR Platform for Enhancing Security with Automation.
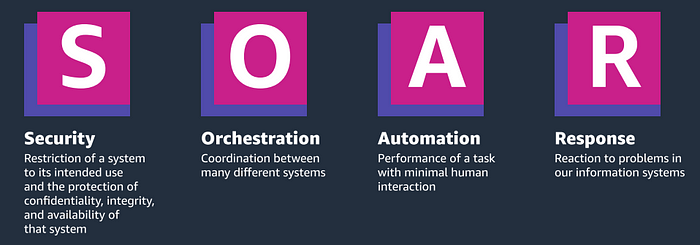
AWS SOAR (Security Orchestration, Automation, and Response) is a framework that enables organizations to automate and orchestrate security tasks and workflows. This can include tasks such as incident response, threat intelligence, and vulnerability management.
AWS provides a range of services that can be used to build a SOAR solution on its platform. Here are a few examples:
- Amazon EventBridge: A service that allows you to easily route and process events from AWS services and external sources, such as security tools and devices. This can be used to collect and aggregate security events and trigger automated response actions.
- AWS Lambda: A service that allows you to run code without provisioning or managing servers. This can be used to create custom functions that can be triggered by…

